Introduction
Privacy concerns have grown with
each improvement of modern information technology (MIT). MIT has made it easy for virtually every
organization to set up a database to track their customers’ habits and
purchases. The Internet has increased the
uneasiness because of the ease that Internet sites have been able to profile
web surfers and share that information with others. However, consumers have taken notice, and they have demanded that
web sites protect their personally identifiable information.
The European Union (EU) countries
have taken one approach. They have imposed
complex procedures directed by powerful institutions in order to protect data,
and they have demanded that other counties follow their lead if they wish to
trade with them. The United States has
rejected the EU demands. Instead, the
US has relied on self-regulation to protect individually identifiable data.
This paper examines the impact of
the EU Privacy Directive on the direction of regulation in the United
States. I begin by reviewing the
history of the European Union and its institutions. Next, I analyze the self-regulatory measures introduced in the
United States. Finally, I conclude that
privacy seal programs offer American Internet Sites (AIS) the best mix of
protecting information and minimizing government intrusion.
Background
In order to appreciate the power
and influence of the EU, it is important to understand the structure of
decision making and the institutions that are involved in enacting those
decisions. First, in this section, I
will review the circumstances and the resulting treaties of post World War II
Europe that forged the EU we know today.
Next, I will describe the institutions and procedures necessary to
implement Community Law.
(1)
Building a Union
After World War II, political and
economic instability left European nations vulnerable.[1] The Soviet Union threatened the sovereignty
of individual European nations, as evidenced by the Czechoslovakian coup d'etat
in 1948 and the Berlin blockade in 1948-1949.[2] Moreover, the Soviet Union developed nuclear
capabilities in the late 1940’s, adding to European instability.[3]
To bring about a stable unified
Europe, western European nations started to get together.[4] In October 1947, twenty-three countries
signed a joint agreement, the General Agreement on Tariffs and Trade (GATT).[5] Thus began the long road to European
unification.
The next important date is
1957. That year, the Treaty of Rome
formed the European Economic Community (ECC), which consisted of six
nation-states: Belgium, France, Germany, Italy, Luxembourg and the Netherlands.[6] The United Kingdom was invited to join, but
chose not to become a member at that time.[7]
The political and economic
success of the ECC, encouraged other nations to join the club.[8] In 1973 the United Kingdom, Denmark, and
Ireland increased the number of member nations to nine.[9] Next, in the 1980’s, came the
"Mediterranean enlargement."[10] Greece joined in 1981 and, in 1986, Portugal
and Spain became members.[11] Finally, in 1995 Austria, Finland and Sweden
signed up.[12]
Today there are fifteen Member
States in the EU.[13] In 1999, the European Union represented
almost $350 billion in trade with the United States. Only Canada had more trade with the US that year.[14]
(2)
Expanding Co-operation
The Treaty on
European Union (TEU), which is sometimes referred to as the Treaty of
Maastricht, became effective in 1993.
The TEU formally restructured the ECC into the European Union. The TEU, Article 2, states the purpose of
the EU:
The Community shall have as its task, by
establishing a common market and an economic and monetary union and by
implementing common policies or activities referred to in Articles 3 and 4, to
promote throughout the Community a harmonious, balanced and sustainable
development of economic activities, a high level of employment and of social protection,
equality between men and women, sustainable and noninflationary growth, a high
degree of competitiveness and convergence of economic performance, a high level
of protection and improvement of the quality of the environment, the raising of
the standard of living and quality of life, and economic and social cohesion
and solidarity among Member States.[15]
(3)
Institutions of the Union
The TEU establishes institutions
and procedures “necessary to achieve the objectives” of the Treaty.[16] There are three Institutions involved in
formulating much of the EU’s policies and direction,[17]
the European Parliament (the “Parliament”), the Council of the European Union
(the “Council”), and the European Commission (the “Commission”).[18] I will summarize the responsibilities of
each.
The European Parliament
The Parliament is a directly
elected democratic institution[19]
and represents 370 million citizens.[20] The Parliament’s “primary objectives are . .
. to pass good laws and to scrutinize and control the use of executive power.”[21] To accomplish these objectives the
Parliament has three important powers: legislative power, budgetary power, and
oversight power.[22] I will address each in turn.
Legislative Power:
Originally, the Parliament had
only a consultative role.[23] Today, in addition to their consultative
role, the Parliament has the power to amend and adopt certain legislation.[24] For issues that relate to the internal
market, consumer protection, trans-European networks, education, health, and
other related issues, legislation is adopted jointly by the Parliament and the
Council.[25] This two tiered decision making procedure is
known as "co-decision making".[26]
In addition, the Parliament has a
role in appointing the President of the Parliament and the members of the Commission.[27]
Budgetary Power:
The Parliament approves the
Union’s yearly budget.[28] By withholding its approval, the Parliament
may exercise authority in how funds are distributed, thereby giving it
influence over the content of all legislation.[29] The President of the Parliament must sign
the budget to enact it into law.[30]
Oversight Power:
The Parliament has the obligation
to assure that funds are spent for the purposes agreed upon.[31] Moreover, the Parliament has the duty to
prevent and detect fraud.[32]
It is important to note that the
Parliament is the only EU Institution “that meets and deliberates in public.”[33] Nearly all of the decisions in the EU are
done in secret meetings.[34] In fact, all members and former members of
an EU institution are required “not to disclose
information . . . about the undertakings, their business relations or their
cost components.” [35]
The Council of the European Union
The Council is made up of fifteen
Ministers.[36] Each Member State names one Minister.[37] Each Minister is empowered to commit his
Government.[38] In turn, each Minister is politically
accountable to their national parliaments.[39] Ministers attend council meetings that deal
with specific subject areas.[40] Which Minister attends each Council meeting
depends on the subject matter discussed.[41]
The Presidency
The President of the Council
presides over all of the Council meetings.[42] Every six months, the Presidency rotates
according to a set schedule.[43] The President of the Council is to host a
meeting of the European Council (not to be confused with the Council for the
European Union) at least twice a year for a “European Summit.”[44]
The European Council
The European Council is made up
“of the heads of State or Government of each Member State and the President of
the European Union.”[45] The Summit is an informal gathering, where
there are no set procedures.[46]
“The European Council has become
an increasingly important element of the Union, setting priorities, giving
political direction, providing impetus for its development and resolving contentious
issues that have proved too difficult for the Council of Ministers.”[47]
Legislation
The Council (or by the Parliament
and Council if a co-decision is called for) must adopt proposals Law in order
for them to become Community law.[48] There are four forms of Community law:
1.
Regulations: these
are directly applied without the need for national measures to implement them;
2.
Directives: bind
Member States as to the objectives to be achieved while leaving the national
authorities the power to choose the form and the means to be used;
3.
Decisions: these
are binding in all their aspects upon those to whom they are addressed. A decision may be addressed to any or all
Member States, to undertakings or to individuals;
4.
Recommendations and
opinions: these are not binding.[49]
The European Commission
There are twenty members of the
Commission, each member is appointed to a five-year term by their home
governments.[50] The break down of the Commission is:
|
Country
|
Number
|
|
|
Germany
|
2
|
|
Spain
|
2
|
|
France
|
2
|
|
Italy
|
2
|
|
United Kingdom
|
2
|
|
Belgium
|
1
|
|
Denmark
|
1
|
|
Greece
|
1
|
|
Ireland
|
1
|
|
Luxembourg
|
1
|
|
The Netherlands
|
1
|
|
Austria
|
1
|
|
Portugal
|
1
|
|
Finland
|
1
|
|
Sweden
|
1
|
|
|
|
|
|
With 16,000 staff members, the
Commission is the largest Institution of the EU.[51] The Commission meets at least “once a week
to adopt proposals, finalize policy papers and take other decisions required of
it.”[52] Commissioners have a duty to act in the best
interests of the European Union, rather than in the interest of their national
governments.[53]
The Commission has three distinct
functions:
1)
to initiate proposals for legislation;
2)
to be the guardian of the Treaties; and
3)
to execute EU policies and actions.[54]
I will address each function
individually.
Initiate Legislation
The Commission initiates
Community policy and represents the general interest of the European Union.[55] Before the Commission recommends any
legislation, they perform extensive fact gathering. They interview and seek comment from individual governments,
industry representatives, trade unions officials, special interest groups and
technical experts.
The Commission recommends action
on an issue “only when it will be more effective than if [action were left] to
individual Member States.”
Guardian of the Treaties
The Commission acts as the
“guardian of the EU treaties to ensure that EU legislation is applied correctly
by the Member States and that all citizens and participants in the single
market can benefit from the level playing field that has been created.” Where necessary, the Commission takes action
against those in the public or private sector that fail to respect their treaty
obligations. “It can, for instance,
institute legal proceedings against Member States or businesses that fail to
comply with European law and, as a last resort, bring them before the European
Court of Justice.”[56]
Execute EU Policies and Actions
The third function of the
Commission is that of the executive body of the EU.[57] The Commission is responsible for
implementing and managing policy.[58] It manages the Union's annual budget,[59]
runs its Structural Funds[60],
and negotiates trade agreements with third countries.[61]
The Commission has played a
leading role in integrating the Member States, by playing the role of mediator
when disputes arise between members.[62] “Its impartiality and commitment to the
common interest make it an accepted mediator by all sides.”[63]
The Privacy Policy of the EU
In order to accomplish the goals
stated in Article 2 of the TEU, Member States are prohibited from establishing
policies that restrict the import or export of goods among the Member States.[64] In addition, each Member State must
establish laws that facilitate the functioning of a common market.[65]
In 1993, before the TEU, Germany
and France (the two largest economies in the EU) had legislation that protected
their citizens’ data privacy, but several other Member States did not have any
privacy policies in place (like Italy).[66] The disparity in privacy protection among
the Member States threatened to inhibit the flow of data, therefore trade,
among the member nations.[67]
To ease concerns, and harmonize
the privacy policies among the EU, the EU enacted Directive 95/46/EC, “on the
protection of individuals with regard to the processing of personal data and on
the free movement of such data.” [68] The European Community Privacy Directive
(the Directive) took effect on October 25, 1998; three years after the
Parliament and the Council passed it.[69]
The Directive begins with the
premise that data protection is a “fundamental right.”[70] In order to protect this fundament right,
the Directive provides:
Member
States shall provide that personal data may be processed only if:
(a)
the data subject has unambiguously given his consent; or
(b)
processing is necessary for the performance of a contract to
which the data subject is party or in order to take steps at the request of the
data subject prior to entering into a contract; or
(c)
processing is necessary for compliance with a legal obligation
to which the controller is subject; or
(d)
processing is necessary in order to protect the vital interests
of the data subject; or
(e)
processing is necessary for the performance of a task carried
out in the public interest or in the exercise of official authority vested in
the controller or in a third party to whom the data are disclosed; or
(f)
processing is necessary for the purposes of the legitimate
interests pursued by the controller or by the third party or parties to whom
the data are disclosed, except where such interests are overridden by the
interests for fundamental rights and freedoms of the data subject which require
protection under Article 1 (1).
The Directive was designed to
foster economic trade between the Member States of the European Union. Ironically, the Directive that was designed
to foster trade, may work to disrupt trade between the EU and “third
countries,” most notably the United States.
Article 25 of the EU Privacy
Directive states:
Transfer to a third country of
personal data which are undergoing processing or are intended for processing
after transfer may take place only if . . .the third country in question
ensures an adequate level of protection.
Where a country is found to have
inadequate protection, Article 26 spells out a list of exceptions that may
allow the transfer of data despite inadequate countrywide protections. Article 26 says:
.
. . transfers of personal data to a third country which does not
ensure an adequate level of protection within the meaning of Article 25 may
take place on condition that:
1) unambiguous consent
2) performance of a K
3) K in interest of data subject
4) public interest
5) vital interest
6)
according to law or regulation
2) Without
prejudice to paragraph 1, a Member State may authorize a transfer or a set of
transfers of personal data to a third country which does not ensure an adequate
level of protection within the meaning of Article 25 (2), where the controller
adduces adequate safeguards with respect to the protection of the privacy and
fundamental rights and freedoms of individuals and as regards to exercise of
the corresponding rights; such safeguards may in particular result from
appropriate contractual clauses.
Because the proffered protections
are in the form of a “Directive,” they do not apply directly to individual
Member States. Each Member State must
take measures to implement the Directive into national legislation. However, the Directive does establish new
institutions for “coordinating the enforcement authorities of the fifteen
nations.”[71] In addition, each Member State must erect
one or more privacy agencies to monitor their national privacy policy.[72]
Privacy Protection in the United States
In the US, privacy protection is
not considered a fundamental right.
Therefore, US privacy laws are not as broad or far-reaching as the
European Union Privacy Directive calls for.
The US data protection laws take a
“sectoral,” [73] some would
say "ad hoc,"[74]
approach. Generally, privacy
protections in the US are limited to the right of the citizen against the
government and do not regulate individual relationships, as does the Directive.[75] Individual relationships are left to private
agreements or self-regulation.[76]
Self-Regulation
Modern information technology,
through the Internet, has created an easily accessible worldwide market. American Internet Sites (AIS) are “open” to
visitors from around the world, including citizens of the EU. Therefore, unless a EU visitor
"unambiguously" gives consent for an AIS to gather, collect and
process personal data, or another narrow exception applies, the AIS will be
barred from using or collecting that data.[77]
Federal privacy regulations in
the United States are not going to be implemented any time soon.[78] Therefore, in order to continue the flow of
information from the EU, it is incumbent upon AISs to self regulate if they
wish to extend their market and avoid government regulation. This section will examine two
self-regulatory practices that may qualify as “adequate” under the
Directive. First I will summarize the
safe harbor proposal. Then, I will
review seal programs.
(1)
Safe Harbor
The American Government has
addressed this threat to trade by negotiating with EU representatives, through
the United States Commerce Department (USCD).[79] The negotiations center on creating a “safe
harbor” for American companies, to “enable them to comply with the requirements
of the European Union's Directive on Data Protection regarding personal data
transfers to third countries.”[80]
On March 14, 2000, after two
years of intense negotiations, the US and EU tentatively agreed on the
principles that the US safe harbor must include in order to be “adequate” under
the Directive.[81]
In order for the safe harbor
arrangement to become effective, the agreement must be approved by a qualified
majority of Member States in the committee established in the Directive.[82] Before seeking the Committee's formal
decision, however, the Commission must consult with the data protection
commissioners of the Member States.[83] Then the Commission must submit the decision
to the European Parliament for approval.[84] Only after the Parliament approves will the
safe harbor become effective.[85] Furthermore, AIS operators must submit to
oversight by the European Data Protection Authorities, the Federal Trade
Commission and the United States Commerce Department.[86]
Soon after the tentative
agreement, the EU balked, declaring that the safe harbor principles “do not go
far enough to protect the rights of the citizens.”[87] Additionally, US groups have protested the
agreement as too intrusive and going too far.[88]
(2)
Privacy Seal Programs
The “adequate” standard set by Article
25 of the Directive is not a clear standard.
Because the standard is not clearly defined, the best way to determine
what constitutes adequate protection is to review the Directive Commission’s
Working Documents to resolve what the EU Commission considers necessary to
establish adequate protection.
This section begins by
establishing what elements comprise adequate protection according to the EU
Commission. Next, I will focus on the
two most popular “Privacy Seal” programs and reveal their elements and
standards. Finally, I will assess
whether these seal programs should qualify for an exemption from the
Directive’s mandates.
What Constitutes "Adequate Protection"?
In 1998, the Working Party of the
EU Data Protection Commissioners[89]
issued a Working Document titled “Transfers of personal data to third
countries: Applying Articles 25 and 26 of the EU data protection directive.”[90] This document lays out the requirements for
answering “all the central questions raised by flows of personal data to third
countries in the context of the application of EU data protection directive.”[91]
The basic principles to be
included are the following:
1. the purpose limitation principle - data
should be processed for a specific purpose and subsequently used or further
communicated only insofar as this is not incompatible with the purpose of the
transfer. The only exemptions to this rule would be those necessary in a
democratic society on one of the grounds listed in Article 13 of the directive.
2. the data quality and proportionality
principle - data should be accurate and, where necessary, kept up to date.
The data should be adequate, relevant and not excessive in relation to the
purposes for which they are transferred or further processed.
3. the transparency principle - individuals
should be provided with information as to the purpose of the processing and the
identity of the data controller in the third country, and other information
insofar as this is necessary to ensure fairness. The only exemptions permitted
should be in line with Articles 11(2) and 13 of the directive.
4. the security principle - technical and
organizational security measures should be taken by the data controller that
are appropriate to the risks presented by the processing. Any person acting
under the authority of the data controller, including a processor, must not
process data except on instructions from the controller.
5. the rights of access, rectification and
opposition - the data subject should have a right to obtain a copy of all
data relating to him/her that are processed, and a right to rectification of
those data where they are shown to be inaccurate. In certain situations he/she
should also be able to object to the processing of the data relating to
him/her. The only exemptions to these
rights should be in line with Article 13 of the directive.
6. restrictions on onward transfers -
further transfers of the personal data by the recipient of the original data
transfer should be permitted only where the second recipient (i.e. the
recipient of the onward transfer) is also subject to rules affording an
adequate level of protection. The only exceptions permitted should be in line
with Article 26(1) of the directive.[92]
Self-Regulation Through Privacy Seal Programs
Privacy Seal programs are third
party companies that place tamper proof logos in a prominent place on a web
site. The seal lets visitors know that
the site has a privacy policy in place and that the company follows the posted
policy. Furthermore, by “clicking” on
the seal, the visitor is taken to the web site’s privacy policy. In addition, the Seal Company provides for
an oversight procedure and a dispute resolution process.
This section analyzes the two
most popular seal programs, both of which were recommended by President Clinton
recently. He challenged AISs “to engage
in effective self-regulation, with enforcement by organizations such as
BBBOnLine and TRUSTe.”[93]
I will take a three-step
approach. First I will summarize the
organizations’ history. Next I will
review their privacy standards, oversight procedures and resolution
processes. Finally, I will compare each
to the organization’s standards to that of the safe harbor, in order to
determine if the standards may qualify as adequate protection under the
Directive.
TRUSTe
TRUSTe is the oldest and largest
of the privacy seal programs. The
TRUSTe program was launched in 1997, with 18 licensed sites.[94] In 1998 the number of participating sites
climbed to 279.[95] Recently, TRUSTe awarded its 1000th
privacy seal to X-Collaboration, a Boston-based software company.[96]

The idea for TRUSTe began during
a lecture on "Trust" in March 1996.[97] Lori Fena, Executive Director of the
Electronic Frontier Foundation (EFF), and Charles Jennings, founder and CEO of
Portland Software were attending that lecture.[98] The two met at that meeting and discussed
the need “for branded symbols of trust on the Internet similar to UL Labs or
Good Housekeeping ‘seals of approval.’"[99] The idea took hold and the two worked
together to institute such a program.[100]
TRUSTe is a non-profit
organization “whose mission is to build users' trust and confidence on the
Internet and, in doing so, accelerate growth of the Internet industry.”[101] To that end, TRUSTe awards its “trustmark”
or seal “to Web sites that adhere to established privacy principles and agree
to comply with [TRUSTe’s] oversight and consumer resolution process.”[102]
Privacy Policy
In order to be awarded a TRUSTe
seal a web site must adopt a privacy statement that discloses, at a minimum:
¨
What personal information is being gathered.
¨
Who is collecting the information.
¨
How the information will be used.
¨
With whom the information will be shared.
¨
The choices available to users regarding collection,
use, and distribution of their information: You must offer users an opportunity
to opt-out of internal secondary uses as well as third-party distribution for
secondary uses.
¨
The security procedures in place to protect users'
collected information from loss, misuse, or alteration: If your site collects,
uses, or distributes personally identifiable information such as credit card or
social security numbers, accepted transmission protocols (e.g. encryption) must
be in place.
¨
How users can update or correct inaccuracies in their
pertinent information: Appropriate measures shall be taken to ensure that
personal information collected online is accurate, complete, and timely, and
that easy-to-use mechanisms are in place for users to verify that inaccuracies
have been corrected.[103]
Oversight Procedure
TRUSTe uses a three tiered
oversight procedure: initial and periodic review, “seeding,” and community
monitoring.[104] I will address each procedure separately.
(a) Initial and Periodic Review
Before a potential licensee can
complete a TRUSTe application, the applicant must have a privacy policy in
place.[105] In order to assist the applicant, TRUSTe
provides a “Privacy Policy Wizard.”[106] The wizard tailors a policy based on answers
to questions it poses regarding the specific privacy practices of the
applicant’s web site. Next, the
applicant is asked to perform a self-assessment of their internal privacy and
security practices.[107]
After that, a TRUSTe
representative conducts a review and certification process, to ensure that the
stated policy is accessible to visitors and meets the stated requirements.[108] Once an applicant’s site has been approved,
a TRUSTe representative periodically reviews the site to ensure that it
continues to comply with the posted privacy practices and program requirements.[109] The representative also checks for changes
to the site’s privacy policy.[110]
(b) Seeding
In order to verify that a site is
compiling with its privacy policy, TRUSTe submits unique identifiers to the web
site.[111] The web site does not know which submissions
are genuine and which is a “seed” planted by TRUSTe.[112] Then, TRUSTe monitors the seeded identifier
to ensure that the site is “practicing information collection and use practices
that are consistent with its stated policies.”[113]
(c) Community Monitoring
TRUSTe also relies on visitors of
the web site to “report violations of posted privacy policies, misuse of the
TRUSTe trustmark, or specific privacy concerns pertaining to a licensee.”[114] After all, the visitors of the web site are
the parties that are protected by the TRUSTe program.[115] If they want to voice a complaint or concern
about the privacy practices of a licensed web site, they need only submit a
“Watchdog reporting form” and TRUSTe will follow up on the report.[116]
Resolution Processes
A complaint or concern may arise because of a complaint from a visitor or
from TRUSTe’s monitoring program.[117] To address complaints, TRUSTe uses a
three-tier approach.[118] First, they rely on the licensee and the
complainant to resolve the dispute per the posted privacy policy.[119] Second, if the parties can not reach an
agreement, TRUSTe acts as a “liaison between” parties to resolve the issue.[120] This process entails:
¨
Notifying the
licensee of the consumer's complaint and working with the site for a speedy,
satisfactory resolution.
¨
Notifying the
consumer of the resolution or other relevant findings.
¨
Pursuing the issue
further if we are unable to reach a mutual resolution with the licensee.[121]
If TRUSTe determines that the licensee has violated its posted privacy
practices or other TRUSTe program requirements, “we will conduct an escalating
investigation. This process may include
an on-site compliance review by one of
TRUSTe's official auditors”[122] Then TRUSTe will work with the licensee to
bring the web site into compliance.[123] Failing that, TRUSTe may:
¨
revoke the
licensee’s use of the TRUSTe Seal,
¨
terminate the
licensee from the program, or
¨ refer the matter to the appropriate government
agency.[124]
BBBOnLine
BBBOnLine is a wholly owned
subsidiary of the Council of Better Business Bureaus.[125] The program was launched on March 17, 1999
and features a Privacy mark that is a padlock with a globe in the middle. BBBOnLine quickly awarded 100 web sites a
seal by September 1999. Today, just
over one year after launching the program, BBBOnLine has over 400
licensees.

The Better Business Bureau hopes
to leverage their 86 year history of assisting business with self-regulation
and dispute resolution into a mark that will be trusted by the public. In developing the program, BBBOnLine sought
out e-commerce business leaders and representatives from major
corporations. The initial participants
included leaders in the e-commerce arena.[126]
“BBBOnLine's mission is to
promote trust and confidence on the Internet.”[127] The BBBOnLine Privacy Program features
verification, monitoring and review, consumer dispute resolution, and
enforcement mechanisms.
Privacy Policy
In order to be awarded a
BBBOnLine Privacy Seal, a web site must meet “the highest standards for the
treatment of personally identifiable information in cyberspace.”[128] Furthermore, the posted privacy statement
must be easy to read, in clear and simple language, and it must disclose:
1.
the collector(s) of the information
2.
the type(s) and intended use(s) of the individually
identifiable information being collected
3.
the choices individuals have about the way such information is
used and to whom it is disclosed
4.
the collector’s commitment to data security
5.
an appropriate contact method regarding the web site’s privacy
policy
6.
the seal participant’s participation in the BBBOnLine Privacy
Program and information on how individuals may learn more about that program
7.
any corporate subsidiaries, operating divisions or related
product lines which are excluded from seal coverage
8.
any individually identifiable information collected at the
site which is shared with contractors, corporate affiliates or other third
party agents not covered by a common privacy policy
9.
the choices available to users with regard to information
shared with affiliates or third party agents not covered by a common privacy
policy
10. the
steps the seal participant takes to assure the accuracy of individually
identifiable information that it maintains in identifiable form
11. the
process available to individuals to obtain access to individually identifiable
information collected from them online and the process available to correct
factual inaccuracies in that information
12. if
access to any or all of the web site is conditioned on the disclosure of
individually identifiable information, individuals must be informed of the
consequences of refusing to disclose such data
13. if
the organization merges and/or enhances individually identifiable information
with data from third parties for the purposes of marketing products or services
to the individual
14. if
any other organization collects individually identifiable information at the
site as the result of transacting business with the individual at the site
15. that
individuals must contact third party collectors of individually identifiable
information directly for information on the use of their data
16. any
information collection that is not covered by the privacy policy, including,
but not limited to, information collection where the individual submitting the
information is clearly acting only in his/her business capacity
¨
Additionally, the correction process (#10) must employ
an authentication mechanism, which is to be disclosed in the Compliance
Assessment.[129]
TRANSFER OF THIRD PARTY
INFORMATION
Seal participants must have a process in place to make unaffiliated
third parties or corporate affiliates not covered by a common policy practice
aware of the site’s privacy policies when transferring individually
identifiable information to such parties, and must describe that process in
their Compliance Assessment.
Seal participants must require agents or contractors who have access to
individually identifiable information and prospect information to keep the
information confidential and not use it for any other purpose than to carry out
the services they are performing for the organization.
Seal participants may not rent, sell, exchange, or in any manner
transfer information about a prospect submitted by another party to any third
party, unless the third party is an agent or contractor involved in carrying
out the transaction for which the prospect's information was submitted. This prohibition on such transfers applies
without regard to any choices about third party transfers made by the
individual submitting the information.
CHOICE & CONSENT
A seal participant must allow individuals the opportunity to opt-out or
otherwise prohibit unrelated uses of individually identifiable information
about them, that is, uses not disclosed in the privacy policy at the time the
information is collected.
A seal participant must provide individuals with a choice regarding the
transfer of information to third parties for marketing purposes. This may be accomplished through one or more
of the following:
1.
an opt-out opportunity
2.
an opt-in opportunity
3.
through a technological tool for individuals to make choices
about such transfers (The method(s) used must be disclosed in the Compliance Assessment.)
Where the site conditions the granting of access to some or all of its
web site or online services based on the disclosure of individually
identifiable information, the participant must inform individuals in its
privacy notice or at the point of collection of the consequences of refusing to
provide such information.
ACCESS
A seal participant must assure that information collected online is
accurate, complete and timely for the purpose(s) for which it is to be used and
must provide individuals with access to individually identifiable information
collected from them online if such information is retrievable in the ordinary
course of business and providing access does not impose an unreasonable burden.
A seal participant must establish effective and easy to use mechanisms
to permit individuals access to correct inaccurate factual information. A seal participant must take steps to help
assure the accuracy of the individually identifiable information it is
maintaining.[130]
Oversight
A BBBOnLine web site is subject
to an independent and random audit of their information practices. Generally, BBBOnLine relies on the consumer
to discover and report any web site that violates its stated privacy policy,
because the Better Business Bureau is a well-recognized consumer advocate.
Before a web site is awarded a
BBBOnLine seal, BBBOnLine reviews the company's privacy policy, conducts a
comprehensive review, and evaluates the processes the company has in place in
order to live up to the privacy policies they post.
Resolution Process
The BBBOnLine Dispute resolution
process provides for four levels of intervention.[131]
1.
Self Help
First, the web site must publish
a designated person associated with the web site a visitor (complainant) can
contact with a complaint about their privacy policy or their failure to follow
the posted policy. The visitor must try
to resolve the dispute directly with the web site operator.
2.
Privacy Policy Review Service
Second, if the complainant is
unhappy with the result in the first step, or the web site does not answer the
complaint, the complainant may contact the
BBBOnLine Privacy Program Dispute
Resolution Process (DRP). The DRP
provides for review of a complaint by the Privacy Policy Review Service (PPRS)
of BBBOnLine. PPRS forwards the complaint to the web site
(respondent) and requests an answer to the complaint.
The respondent’s answer is forwarded to the complainant for a reply. If the respondent submits a reply, the
respondent may respond to the reply. In
addition PPRS may request information from either party. Using the information in the case file[132]
the PPRS “shall formulate its judgment on the merits of the case in a statement
of ‘findings, recommendations and conclusions’ including any necessary
corrective action and a time frame for such action.”
Each decision is provided to the parties, and made available to the
public on BBBOnLine.
3. Filing
an Appeal
The complainant or respondent may seek an appeal by
submitting a letter requesting an appeal to the Privacy Review Appeals Board
(PRAB), “within 5 business days of receipt of the final case decision.” The letter shall specify the issues the
party wishes to appeal, state whether the appeal is sought as of right or on
discretionary grounds, and explain how the appeal qualifies on such
grounds.
The appellant must send a copy of the request
letter to the appellee.[133] Then, PRAB will decide “whether the
requested appeal is warranted and advise the parties of its decision.”[134] Again, the decision is published.
4. Notice of
Intent
“If the decision is in favor of the complainant and the respondent fails
to indicate . . . that it intends to take the required corrective action(s),
the Chair shall issue a Notice of Intent to the respondent. The Notice will advise the licensee that the
matter will be referred to the appropriate government agency. “PRAB shall also forward the decision to the
other party and make the decision public.”
Applying the Standard
“[I]t is clear that any meaningful analysis of
adequate protection must comprise the two basic elements: the content of the
rules applicable and the means for ensuring their effective application.”[135] Each of the privacy policies outlined above
meet each and every principle outlined in the Directive’s Working Party
document. Furthermore, each provides
for a resolution process that ensures that a complaint from a data subject will
be addressed and resolved.
Conclusion
This paper has documented the
complex and bureaucratic system that the European Union has imposed on its
citizens in order to protect their privacy.
The EU has threatened to withhold data transfers to third countries that
do not impose that system on the their own citizens, for the benefit of
Europeans.
So far, the US government has
bought into the EU bluff. The Commerce
Department’s safe harbor program is described as self-regulation. However, the only voluntary part of the program
is doing business with EU citizens.
Once a company decides to sell to EU citizens the “self” prefix is gone,
and all that is left is regulation.
Under the safe harbor proposals, a US company must submit to the EU
Privacy Authority, individual Member States Privacy Commission, the United
States Commerce Department, and the Federal Trade Commission, not to mention
the various legal authorities should a dispute arise.
Furthermore, the safe harbor plan
would put the Executive Branch, by way of the Federal Trade Commission, in an
awkward position. A United States
Federal agency would be in the job of protecting the “fundamental rights” of EU
citizens to the detriment of American citizens. In addition, the safe harbor proposal encourages AIS to set up a
dual system of privacy protection, one for EU citizens and another for everyone
else.
The American approach of true
self-regulation is already working. In
two short years, the number of top sites that post a comprehensive privacy
policy has increased thirty-fold.[136] Two years ago an FTC study discovered that
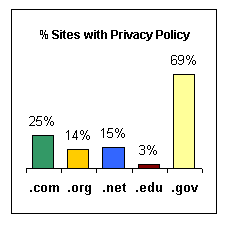
less than 2% of .com top level domains had a comprehensive Privacy Policy in
place. The most recent study conducted
by enonymous.com, found that almost twenty-five percent now have such a policy
in place.[137]
I have surveyed the top two
privacy seal programs, but there are others, and more sites sign on with a seal
program everyday.[138]
As I have illustrated here, the
privacy policies and enforcement procedures offered by sites that are licensed
by these two seal programs exceed the requirements of the EU to qualify for an
exemption under Article 26(2). In
addition, because the privacy policy is easily accessible by clicking on the
privacy seal, a visitor should be considered informed whether they choose to
read the policy or not. Therefore,
should an EU citizen volunteer personally identifiable information to a site
displaying a privacy seal, the submission should be considered “unambiguous
consent” necessary to qualify under the Article 26 (1)(a) exception.
The self-regulatory market system
has worked. If visitors to web sites refuse
to provide personally identifiable information unless a web site lives by a
comprehensive privacy policy, even more sites will adopt such a policy. There is no need for the heavy hand of
government when the invisible hand of the market is at work.
[1] Flaherty and
Lally-Green, The European Union: Where is
it Now? 34 Duq. L. Rev. 923, 928 (1996).
[6] Roger J.
Goebel, The European Union Grows: The
Constitutional Impact Of The Accession Of Austria, Finland And Sweden, 18
Fordham Int'l L.J. 1092, 1094 (1995).
[13] There was
hope that there would be “sweet
sixteen.” But the Norwegian people
defeated a national referendum, and, therefore, did not become a European Union
member state. Id. at 1093.
[14] The United
States only had one larger trading partner in 1999, Canada (nearly $370
billion). See, Privacy Policies that Restrict Transborder Data Flow, at slide
3 (visited April. 29, 1999)
<http://www.it-lawyer.com/school/tbdf/slideshow.html>. Citing U.S. Census Statistics.
[15] Treaty on
European Union, Article 2 (1993).
[17] There are
more than 3 institutions of the EU. In
addition to the European Parliament, The Council of European Union and The
European Commission, there is the Court of Justice, the Court of Auditors, trhe
European Investment Bank, the Economic and Social Committee, the Committee of
the Regions, the European Ombudsman and the European Central Bank. See,
Europa, Institutions of the European
Union (visited April. 29, 1999) <http://europa.eu.int/inst-en.htm>.
[19] Id. at European Parliament.
[20] Id. at European Parliament.
[26] See, Council of the European Union,
General Information (visited April. 29, 1999)
<http://ue.eu.int/en/Info/index.htm>.
[31] Id. at Oversight Power.
[33] How the
European Parliament works, (visited April. 29, 1999)
<http://www.europarl.eu.int/presentation/en/how.htm>.
[35] The members of the
institutions of the Community, the members of committees, and the officials and
other servants of the Community shall be required, even after their duties have
ceased, not to disclose information of the kind covered by the obligation of
professional secrecy, in particular
information about undertakings, their business relations or their cost
components. TEU Article 287 (ex Article 214).
[36] See, Council
of the European Union, General Information, Composition (visited April. 29,
1999) <http://ue.eu.int/en/Info/index.htm>.
[39] See, Council
of the European Union, General Information, Composition (visited April. 29,
1999) <http://ue.eu.int/en/Info/index.htm>.
[42] See, Council
of the European Union, General Information, Presidency (visited April. 29,
1999) <http://ue.eu.int/en/Info/index.htm>.
[43] The order
of the Presidency:
|
|
1st
Half of Year
(Jan. – June)
|
2nd Half of Year
(July – Dec.)
|
|
2000
|
Portugal
|
France
|
|
2001
|
Sweden
|
Belgium
|
|
2002
|
Spain
|
Denmark
|
|
2003
|
Greece
|
|
(visited April 29, 2000)<http://>. See also, Article 203 (ex Article
146). The office of President shall be
held in turn by each Member State in the Council for a term of six months in
the order decided by the Council acting unanimously. TER Article 203.
[44] See also, Article 203
(ex Article 146).The office of President shall be held in turn by each
Member State in the Council for a term of six months in the order decided by
the Council acting unanimously. TEU
Article 203.
[45] See, The Council of the European Union,
(visited April 29, 2000) <http://europa.eu.int/inst/en/cl.htm>.
[46] See, The Council of the European Union,
(visited April 29, 2000) <http://europa.eu.int/inst/en/cl.htm>.
[47] See, The Council of the European Union,
(visited April 29, 2000) <http://europa.eu.int/inst/en/cl.htm>.
[48] See, The Council of the European Union,
Legislation (visited April 29, 2000)
[49] See, The Council of the European Union,
Legislation (visited April 29, 2000)
<http://europa.eu.int/inst/en/cl.htm>.
[50] See, The European Commission, Role of the
European Commission (visited April
29, 2000) <http://europa.eu.int/comm/role_en.htm>.
[52] See, The European Commission, Role of the
European Commission (visited April
29, 2000) <http://europa.eu.int/comm/role_en.htm>.
[53] See, The European Commission – The driving
force for European union, Members of the Commission (visited April 29,
2000) <http://europa.eu.int/inst/en/com.htm>.
[56] See, The European Commission – The driving
force for European union, Guardian of the Treaties (visited April 29, 2000)
<http://europa.eu.int/inst/en/com.htm>.
[59] The
Commissions budget was almost 97 billion in 1999.
[60] The
Structural fund’s main purpose is to even out economic disparities between the
richer and poorer parts of the EU.
[61] The EU has
agreements with more than 100 third countries.
See, Role of the European
Commission, at As the Union's executive body, the Commission manages policies
and negotiates international trade and cooperation agreements. (visited April 30, 2000)
<http://europa.eu.int/comm/role_en.htm>.
[64] Treaty of
European Union, Article 3 (1)(a) (1993).
[65] Treaty of
European Union, Article 3(1)(h) (1993).
[66] Swire &
Litan, None of Your Business World Data
Flows, Electronic Commerce, and the European Privacy Directive. Brookings
Institution Press at 23.
[68] EU
Directive: Directive 95/46/EC of the European Parliament and of the Council of
24 October 1995 on the protection of individuals with regard to the processing
of personal data and on the free movement of such data. Official Journal L 281 , 23/11/1995 p. 0031
- 0050
[70] See,Directive 95/46/EC, Article 1.
[71] Swire &
Litan, None of Your Business World Data
Flows, Electronic Commerce, and the European Privacy Directive. Brookings
Institution Press at 38.
[73] See, Reidenberg, Restoring Americans' Privacy in Electronic Commerce, 14 Berkeley
Tech. L.J. 771, 773 (1999).
[74] Heydrich, A Brave New World: Complying With The
European Union Directive On Personal Privacy Through The Power Of Contract,
25 Brooklyn J. Int'l L. 407, 414 (1999).
[75] Heydrich, A Brave New World: Complying With The
European Union Directive On Personal Privacy Through The Power Of Contract,
25 Brooklyn J. Int'l L. 407, 416 (1999).
[77] See, Sinrod, Reyna, & Barak Enabling Electronic Commerce: Trademark,
Privacy & Internet Business: The New Wave Of Speech And Privacy
Developments In Cyberspace, 21 Hastings Comm. & Ent. L.J. 583, 596
(1999).
[79] Ambassador
David L. Aaron, Letter to Colleagues
(Mar. 17, 2000) <http://www.ita.doc.gov/td/ecom/aaron317letter.htm>.
[80] Ambassador
David L. Aaron, Letter to Colleagues
(Mar. 17, 2000) <http://www.ita.doc.gov/td/ecom/aaron317letter.htm>.
[81] Ambassador
David L. Aaron, Letter to Colleagues
(Mar. 17, 2000) <http://www.ita.doc.gov/td/ecom/aaron317letter.htm>.
[82] European
Privacy Directive Article 31(1995).
[83] European
Privacy Directive Article 29(1995).
[86] Ambassador
David L. Aaron, Letter to Colleagues
(Mar. 17, 2000) <http://www.ita.doc.gov/td/ecom/aaron317letter.htm>.
[87] David
Bicknell, EU Stalls On Us Data Privacy
Deal, Computer Weekly (April 13, 2000)
<http://www.computerweekly.com/cwarchive
/news/20000413/cwcontainer.asp?name=C17.html>
[88] See, Sylvia Dennis, EU/US Data Privacy Pact Continues to Ebb, Newsbytes April 6, 2000
[89] The working
party was established under Article 29 of the Data Protection Directive
[90] See, Media,
Information Society and Data Protection, at Transfers of personal data to third countries : Applying Articles 25
and 26 of the EU data protection directive. (July 24, 1998)
<http://europa.eu.int/comm/internal_market/en/media
/dataprot/wpdocs/wp12en.htm>
[91] See, Media,
Information Society and Data Protection, at Transfers of personal data to third countries : Applying Articles 25
and 26 of the EU data protection directive. (July 24, 1998)
<http://europa.eu.int/comm/internal_market/en/media
/dataprot/wpdocs/wp12en.htm>
[92] See, Media,
Information Society and Data Protection, Transfers of personal data to third countries : Applying Articles 25
and 26 of the EU data protection directive at What Constitutes Adequate
Protection? (July 24, 1998)
<http://europa.eu.int/comm/internal_market/en/media
/dataprot/wpdocs/wp12en.htm>
[93] President Clinton And Vice President Gore:
America’s Agenda For The Information Age, (March 3, 2000) <
http://www.whitehouse.gov/WH/New/html/20000303_2.html>.
[94] TRUSTe Approves 1000th Web Site (visited
May 1, 2000) <http://www.truste.org/about/about_1000th.html>
[96] TRUSTe Approves 1000th Web Site (visited
May 1, 2000) <http://www.truste.org/about/about_1000th.html>
[101] Frequently Asked Questions, What is TRUSTe?
What is its mission? (visited May
1, 2000) <http://www.truste.org/about/about_faqs.html>
[103] See, TRUSTe Program Principles (visited
May 1, 2000) <http://www.truste.com/webpublishers/pub_principles.html>
[104] TRUSTe Oversight at Seeding. (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_oversight.html>.
[111] TRUSTe Oversight at Seeding. (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_oversight.html>.
[112] TRUSTe Oversight at Seeding. (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_oversight.html>.
[113] TRUSTe Oversight at Seeding. (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_oversight.html>.
[114] TRUSTe Oversight at Community
Monitoring. (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_oversight.html>.
[117] See, Resolution
Process (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_recourse.html>
[121] See, Resolution
Process (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_recourse.html>
[122] See, Resolution
Process (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_recourse.html>
[124] See, Resolution
Process (visited May 1, 2000)
<http://www.truste.org/webpublishers/pub_recourse.html>
[126] The companies included America Online,
American Express, AMR Corporation (American Airlines & Travelocity),
AT&T, BankAmerica, Dell, Dun & Bradstreet, Eastman Kodak, Equifax,
Experian, Ford, Hewlett-Packard, IBM, Intel, J.C.Penney, MCI WorldCom,
Microsoft, New York Times Electronic Media, Procter & Gamble, Reed Elsevier
(parent company of LEXIS-NEXIS), Sony, US West, Viacom, and Xerox.
[127]
<http://www.bbbonline.org/about/FAQs.html>
[128] See, BBBOnLine
FAQs at BBBOnLine Privacy <http://www.bbbonline.org/about/FAQs.html>
[129]
<http://www.bbbonline.org/businesses/privacy/eligibility.html>
[130] See, Eligibility Criteria for BBBOnLine
Privacy Seal, Policy Content.
(visited May 1, 2000)
<http://www.bbbonline.org/businesses/privacy/eligibility.html>.
[131] See, BBBOnLine Privacy Program Dispute
Resolution Process Procedures Privacy Policy Review Service and Privacy Review
Appeals Board at § 1.1. (Feb. 11, 1999)
<http://www.bbbonline.org/businesses/privacy/dr/index.html>.
[132] The file
includes the complaint, the answer, the reply, the response to the reply and
any information requested by PPRS the is not confidental.
[133] 4.3.1 Filing an
appeal
[134] 4.3.1 Filing an
appeal
[135] See, Media,
Information Society and Data Protection, Transfers of personal data to third countries : Applying Articles 25
and 26 of the EU data protection directive at What Constitutes Adequate
Protection? (July 24, 1998)
<http://europa.eu.int/comm/internal_market/en/media
/dataprot/wpdocs/wp12en.htm>
[136] The FTC
conducted a survey in 1997 and concluded that less than 2% of all .com web
sites had a comprehensive privacy policy compared to almost 25% in 1999. See,
Internet Privacy: a summary of privacy ratings research by enonymous.com. (visited May 1, 2000)
<http://www.privacyratings.org/research.htm>.
[137] The FTC
conducted a survey in 1997 and concluded that less than 2% of all .com web
sites had a comprehensive privacy policy compared to almost 25% in 1999. See,
Internet Privacy: a summary of privacy ratings research by enonymous.com. (visited May 1, 2000)
<http://www.privacyratings.org/research.htm>.
[138] In
addition to TRUSTe and BBBOnLine there is CPAWebTrust , PrivacyBot,
SecureAssure, and BetterWeb just to name a few.




